Could your business survive a $500,000 loss? According to a report from Cisco, you might not have a choice if your company falls victim to a cyber attack.
Despite reports like these, so many small businesses ignore the dangers of cyber attacks. You take a “that would never happen to me” mindset because all of the stories you hear about ransomware and data breaches point to Fortune 500 companies.
But there’s something you need to know. Studies show that 58% of all cyber-attacks target small and medium-sized businesses (SMBs).
Unlike bigger businesses that invest heavily in managed firewalls, professionally-monitored intrusion protection and disaster recovery planning, and managed phishing services from expensive, certified security pros in state-of-the-art data centers, you’re an easy target for attackers.
All it takes is one unsuspecting employee in your organization to click a malicious link in a phishing email and attackers will have all the information they need to compromise your business.
Even as I write all of this, you still might think this could never happen to you. And that’s why I want to share this story about a customer who (before working with Zero1zero Innovations) nearly put her marketing firm out of business with one click.
It can happen to you and you need to be ready to protect yourself.
Part 1: The Background
We’re not going to name names in this story, so we’ll call the small business owner Susan Smith. Her small, boutique marketing firm has 10 employees and a number of 1099 of subcontractors who help build robust marketing plans for banks and hospitals around the country.
Because she works so closely with banks and hospitals, her firm is very familiar with regulatory compliance and goes out of its way to follow security best practices. The firm has firewalls in place, backup solutions protecting data, and ongoing security monitoring.
And yet, they still got hit by a cyber-attack.
Susan’s team uses Office 365 in the cloud for its convenience, cost efficiency/flexibility, and security. The platform touches every aspect of their business—from Teams where collaborative projects are executed across time zones to Office applications like Word, Excel, PowerPoint, and Outlook. And like most businesses, email is their most heavily utilized tool in the productivity suite.
On a Monday morning at 8:31 AM, Susan got an email while she was traveling that looked like this:
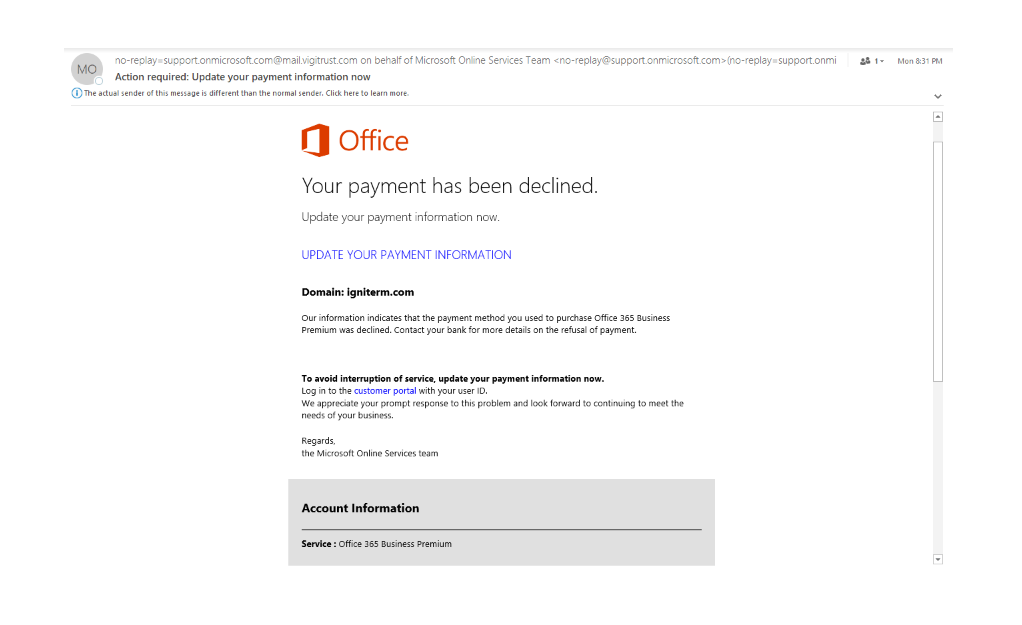
Her bookkeeper took care of billing and since she had several subscription services running in the cloud, Susan thought a credit card had expired. At first glance, the email had a few key elements that made it look legitimate:
Susan sent her bookkeeper to make sure the O365 subscription was up to date and forgot about the email. That is, until a week later when she received a follow-up email.
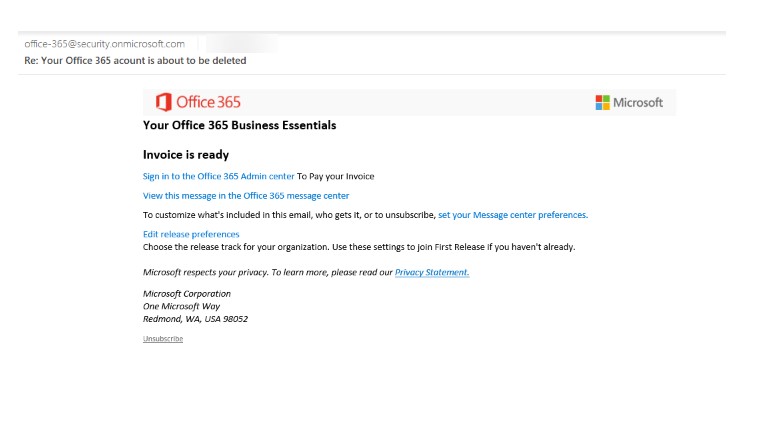
When Susan saw this email, she forwarded it to her bookkeeper again to confirm their Office 365 subscription was current. But she was curious. She wondered how much money they were spending on O365 each month—it was a fleeting thought prompted by the promise of an invoice in the email.
She hovered over the link to make sure it wasn’t a zero phishing scam, saw the usual privacy statement from Microsoft, and clicked the link. She landed on a familiar Office 365 login page:
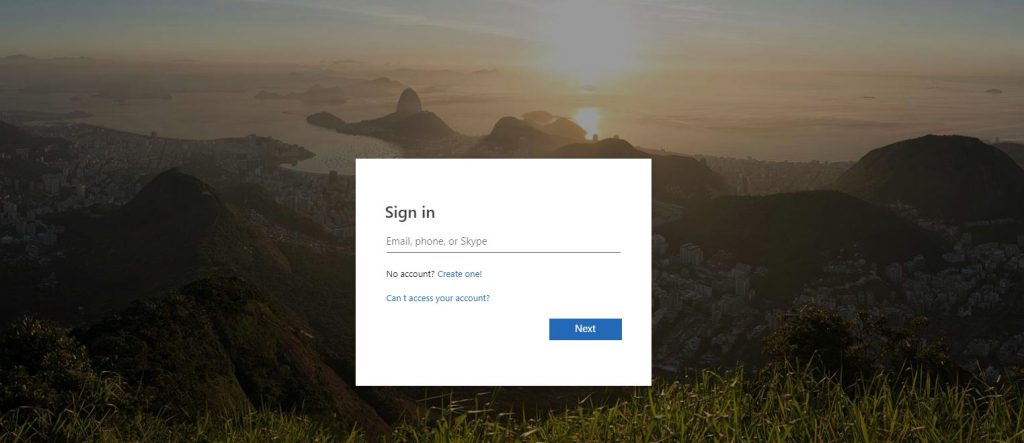
She entered here credentials, clicked again, and the nightmare began. She ended up on a page with a link that read “electriccompany.microsoft…”
Susan knew instantly that she was tricked. And as she came to that realization, the bookkeeper emailed her back and said all payments had been current.
The bookkeeper later emailed and said, “Be careful, that might be a phishing scam.” But it was already too late.
Part 2: Being Hacked
For the next 27 days, Susan and her small business were forced to deal with the fallout of this phishing scam. If you’ve never experienced one, here’s what you could have to look forward to.
- Days 1-4: Susan changed all of her passwords and business continues as usual. She breathed a sigh of relief and hoped she had avoided costly consequences.
- Day 5: Susan opened Outlook and started sending off emails, only to have them returned to her inbox as “undelivered.” As a small business owner, Susan receives upwards of 500 emails per week and she manages all of her time from within her Outlook calendar and email tasks. This problem became frustrating very quickly. She escalated to Tier 2 support and was forced to sit back and wait.
- Day 6: Outlook received emails but Susan still couldn’t send any. After another 3 hour troubleshooting call, she was told to implement the Microsoft Authenticator app for two-factor authentication across accounts.
- Day 7: Susan had to start sending emails from her personal Gmail account. Clients were confused and emails were piling up in her inbox. Her hosting company recommended calling Microsoft directly. And after 2.5 hours on a call, she confirmed that 21,000 emails were sent from her account on Day 4, which prompted Office 365 to suspend her account. The Microsoft reps promised to escalate her to their supervisors and get back to her the next day.
- Days 8-11: No calls came from Microsoft. She could receive Outlook emails, but still couldn’t send them. Susan started to get desperate, wondering whether she should shut down the email account and reopen later. She had to follow up with Microsoft and was told she’d get a call the next day.
- Days 13 and 14: No calls came from Microsoft.
- Day 15: Susan called Microsoft herself—again—and spend 5 hours on the phone testing and trying to identify the problem. All of that to learn that she needed to write a letter to the compliance board at Microsoft explaining what happened and asking to have the email account unlocked.
- Day 18: Susan submitted her letter to the Microsoft Compliance Board saying her credentials had been compromised. She had never sent mass marketing emails in the past and had an 8-year account history of never having a problem like this.
- Days 19-21: There was still no response from Microsoft. Susan was worn out and disheveled from this whole mess. Her emails were being received by Outlook and sent from Gmail—it looked unprofessional and was impacting her ability to schedule teleconference meetings with anyone outside her organization. For a small business owner sending 500+ emails per week, this was a serious issue.
- Day 22: Susan called Microsoft asking for an update, spent 45 minutes on the phone, and was told her case was under review.
- Day 26: Susan called Microsoft begging for help, only to have her request escalated to another supervisor.
- Day 27: Susan’s email is finally reinstated with a warning that if she experiences another incident, her account might not be reactivated.
27 days, 17.5 hours on the phone, and more than 300 emails sent between Gmail and Outlook. Finally, Susan regained control of her Outlook account.
But still, the attackers gained access to an address book of 1,200+ contacts and were likely selling it on the black market. And worse yet, the attackers continued to launch phishing emails to compromise Susan’s employees. Here’s an example of the type of email sent:
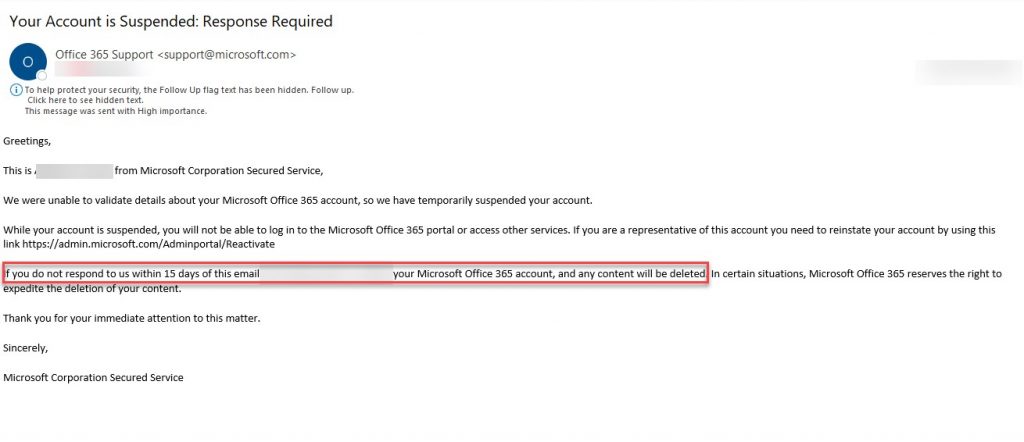
Part 3: Dissecting What Happened
After this whole ordeal, Susan reached out to Zero1zero Innovations to make sure this never happened again. We had the opportunity to go back and look at the emails to see if we could spot the warning signs that this was a phishing email scheme.
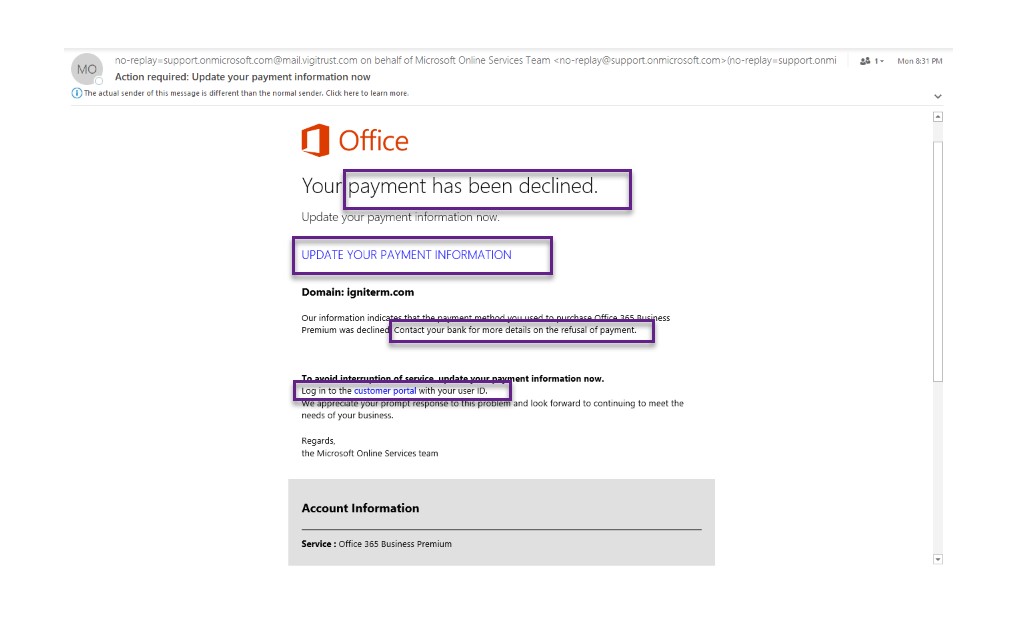
Here’s what we saw when we examined the original emails.
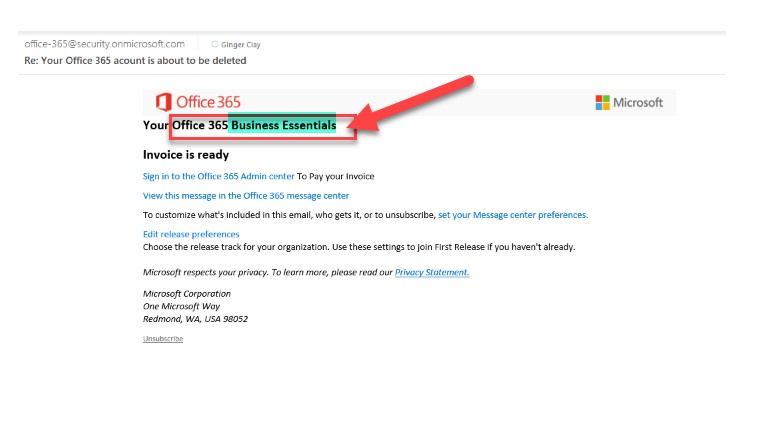
We highlighted the areas that reveal some phishing email clues. First, look at who was actually sending this email. Then, ask yourself—was I enrolled in a Business Premium account, a Business Essentials package, or neither? If something doesn’t match, you shouldn’t click anything.
And when you compare the login pages that stole Susan’s credentials side by side, you can see where the URLs differ:

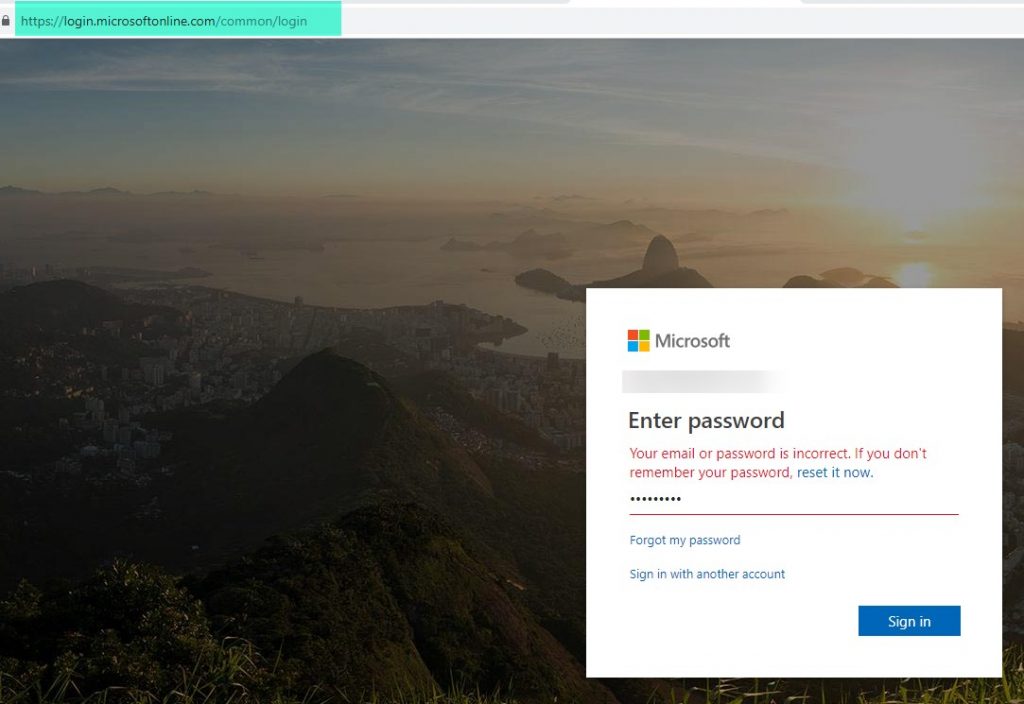
There’s no denying that these warning signs are subtle. Attackers are getting better and better at disguising their phishing emails. So, even if you have strong security solutions and policies like Susan’s company, you could fall victim to a cyber attack.
Would you be able to withstand the frustrations and damaged client relationships that Susan and her company went through? Even if you could, you don’t want to. And that’s why every small business needs a plan to prevent these kinds of zero phishing scams from succeeding.
How to prevent Phishing Emails from ever happening to you?
You can’t stop attackers from ever targeting your business with phishing scams. But you can detect (and recover from) breaches faster with the Cyber Guard.
Our experienced security team monitors and manages your environment 24/7, using leading technology and advanced analytics to actively search for threats. We study how your business operates, your security posture, and the compliance regulations that govern your business to truly understand how we can safeguard your data. Through a comprehensive vulnerability assessment, we can identify weaknesses and plan appropriate remediation to proactively protect your business.
Zero 1 Zero Innovations managed phishing services hinge on four key pillars:
- Advanced Security Solutions: Preventing advanced attacks isn’t easy. You need to ensure every endpoint device is hardened for threat protection. You need to enforce policies for internal employee downloads online and through email. You need firewalls to block potential threats on individual machines. And you need to constantly monitor network activity to spot even the smallest anomalies. Our advanced security suite protects your network with all of this and more.
- Experience: We have our hands in security every day and we know exactly what to look for to proactively minimize your risk.
- Expertise: Life-long learning is one of our core values. We’re constantly training ourselves across the broader security community to ensure we’re ahead of the latest trends and threats.
- Process: We take advantage of best practices that can only be developed by years of real-world client work.
We also build cyber insurance into our offerings, going beyond traditional policies to guarantee that your systems stay up, running, and secure at all times. With a Cyber Guard program, you get managed threat detection, compliance expertise, 24/7 hunting, and threat monitoring, advanced persistent threat analytics, and more.
If you want to learn more about Phishing Emails and what our Cyber Guard managed security program can do for you, contact us today and find out.